Telecommunications Security Act (TSA): Timescales, Impact and Actions


With the first deadline for the Telecommunications Security Act (TSA) looming, many telecoms/broadband providers are starting the process to further understand the implications and work needed for the TSA. This blog serves as a general guide to those confused about the security framework underpinning the act known as the Code of Practice, and whether this is a legal obligation or a list of recommendations.
The act is designed to set a legally binding minimum set of security standards to address issues from recent breaches where security standards and responsibilities have not been defined, and where implications may fail outside of PCI (Payment Card Industry) or the ICO (Information Commissioners Office).
Whilst you may not have a direct requirement for compliance with the act, your providers or suppliers may have requirements imposed meaning you are brought into the scope of the act. It is also worth noting that OFCOM are understood to be referring to the Code of Practice during Cyber Security incidents.
Depending on your tier (1,2 or 3) you have different timeframes for completion of the stages.
The tiering system places public telecoms providers in one of three tiers, based on their commercial scale:
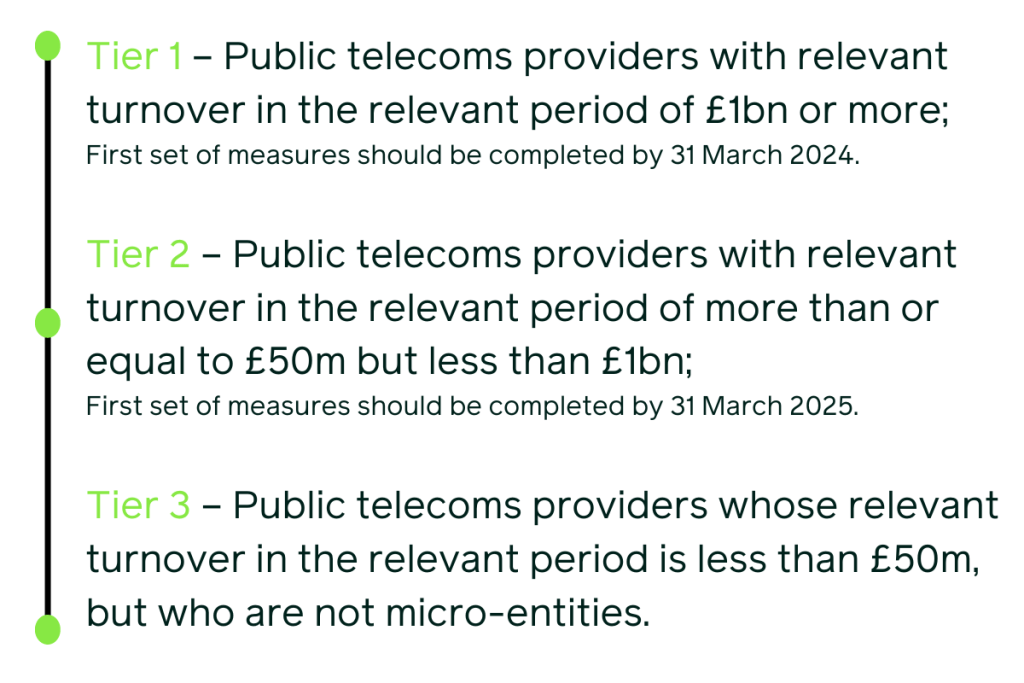
As above, the first set of measures for Tier 1 should be completed by 31 March 2024 and 31 March 2025 for Tier 2. This includes controls M1.01 to M5.07 (Page 74 to page 80 in the Security Code of Practice document).
The Act affects more than just telecom providers, other impacted parties include, network and service providers, ISPs, hardware vendors, software developers and even mobile providers.
This has raised a lot of confusion, and companies are now trying to minimise their third parties as a large percentage of the controls are related to supply chain management and risk assessments of third parties.
Whilst some companies may be unaffected due to their size, with many mergers and acquisitions occurring within the impacted industries these organisations must be aware of the organisational changes that may impact their tier going forward, as well as the systems, processes and third parties which these changes may produce.
Published by the Digital, Culture, Media and Sport (DCMS) and with content from the NCSC;
The main focus for the standard is detecting and responding to a breach, 3rd party and supplier management and management of your network equipment.
This code of practice is not designed to be prescriptive but should be used as a baseline standard with some rough guidance based on the requirements the NCSC are trying to convey.
It’s worth noting that much of this code of practice is taken from the NCSC Cyber Assessment Framework which is becoming a popular framework to simply monitor risk in simple non-technical categories.
OFCOM, the regulatory authority for communications in the UK, has been granted enhanced enforcement capabilities to guarantee the safety and security of the country’s telecommunications networks, ensuring that telecom providers adhere to their security obligations.
For non compliance, a company can be fined up to a maximum of ten per cent of their relevant turnover, or in the case of a continuing failure to comply, £100,000 per day.
The following areas Communicate can provide support, solutions or managed services for:
If you’d like to chat with us about your TSA requirement, please contact us.