Ready to reclaim your credentials?
Monitor over 64,000 locations across the surface, deep and dark web for mentions of your company emails and passwords. Request your free report now:

Monitor over 64,000 locations across the surface, deep and dark web for mentions of your company emails and passwords. Request your free report now:
28%
60%
81%
Over half of attacks use stolen credentials and phishing as their access point.
One leaked password could be used to gain access to your entire digital environment.
Disarm threat actors and seize back your passwords with Stolen Credential Monitoring.
Stolen Credential Monitoring helps you gain insights from world leaders in threat intelligence and keep ahead of criminal organisations by identifying early warning signs and preventing breaches before they occur.
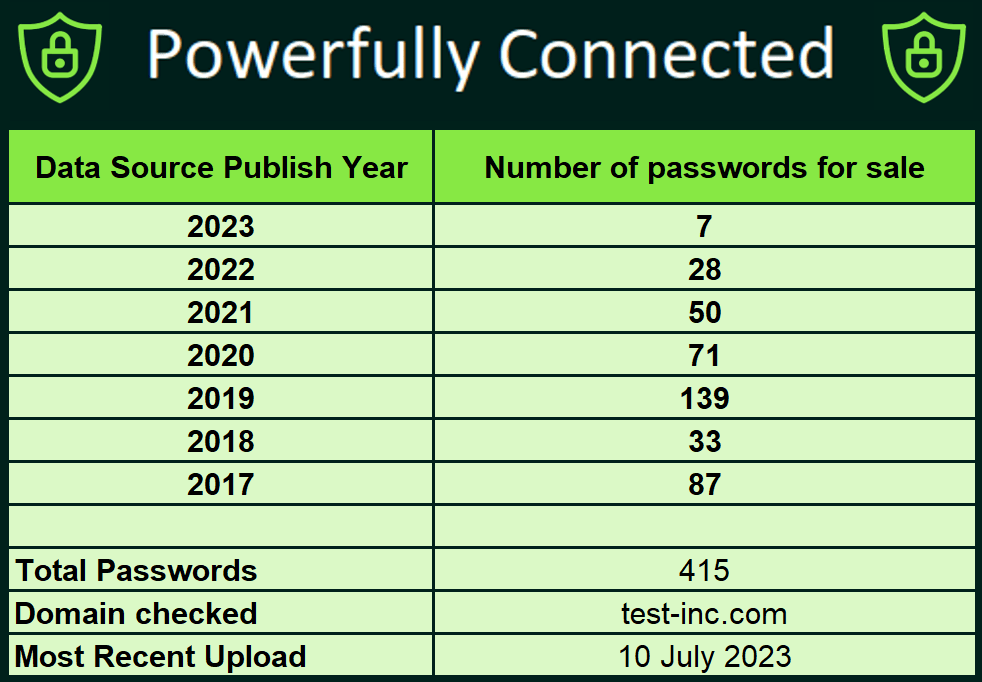
Your organisation and third parties may have active credentials for sale on the deep and dark web right now.
Reduce your digital risk and find out the facts for yourself, before threat actors beat you to it.
Recent examples of leaked passwords include Slack, Google Docs, Office 365, Sage Payroll, VPNs, Banking, CRM systems, Salesforce and social media, . Access your free report now: