What is Incident Response?


Realising that emails are being sent on your behalf, your password has been reset, and you’ve received a ransomware message, what would you do?
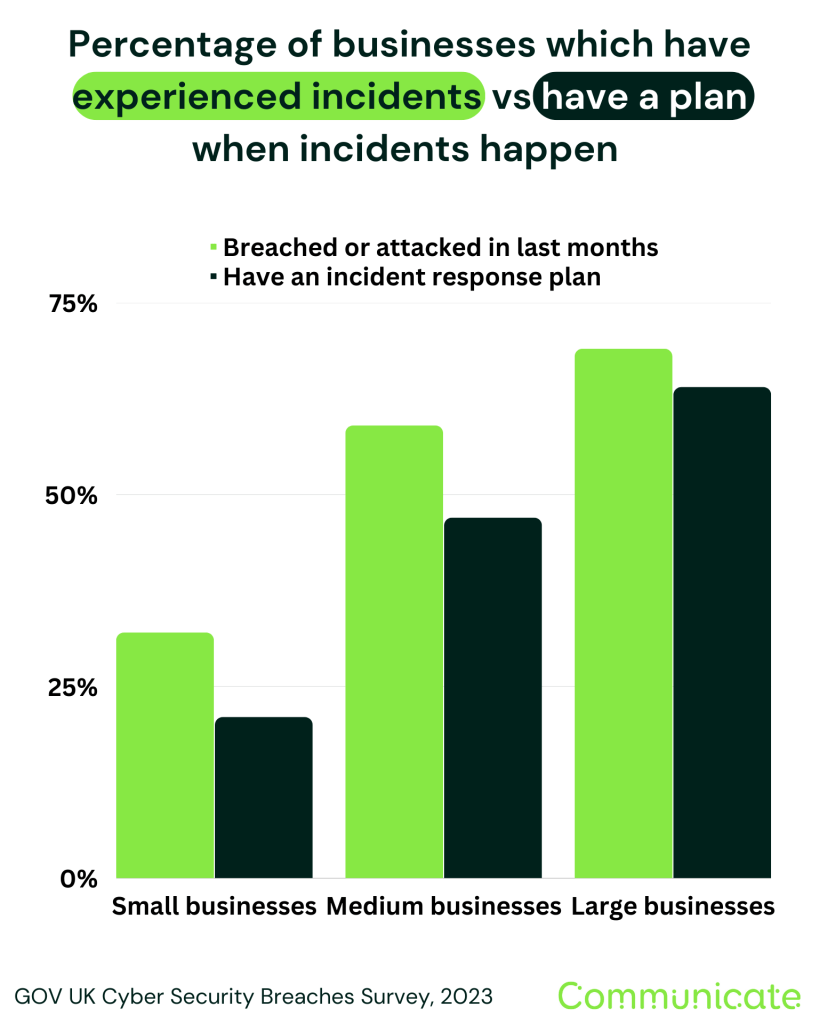
According to the latest Cyber Security Breach Survey from the UK Gov, 73% of businesses do not have a cyber incident response plan, leaving them vulnerable to greater downtime and loss in the case of an incident. This blog will explain what incident response is when it comes to cyber security, and why planning for an incident is important for organisations of all sizes.
A cyber incident as defined by the NCSC is ‘a breach of a systems security policy to affect its integrity or availability and/or the unauthorised access or attempted access to a system or systems.’ This may look like unauthorised access or intrusion into a computer system, network, or data repository to steal, alter, or destroy information, maybe with changes to the firmware or malicious disruption.
An incident may occur as a result of a data breach, a malware attack, a phishing attack, a denial of service attack or an insider threat. Just in the last year, the Royal Mail, T-Mobile, the UK Electoral Commission, 23andMe and the British Library all experienced a public cyber incident, each with varying levels of reputational damage, loss of uptime and data, as well as regulatory fines.
Whilst it’s tempting to believe that only large organisations are at risk, organisations of all sizes found themselves outstripped by the frequency of an incident, compared to the frequency of having an incident response plan, in the latest GOV UK breach survey.
An incident response plan is a document which outlines the processes and responsibilities within an organisation at the point of incident. This might include different phases and activities such as those suggested by the National Institute of Standards and Technology (NIST); preparation, detection and analysis, containment and eradication, and post-incident recovery. This all helps you to spot and remedy incidents to minimise their impact.
Ultimately, the sooner an incident can be detected, contained and eradicated, the more damage is mitigated. Thinking about organisations you’ve seen in the headlines which have experienced a breach, stories that last in the news, with information that shows how it could’ve been avoided or caught earlier, all damages the trust and reputation of that organisation immeasurably.
In addition, concrete costs could include penalties from the Information Commissioner’s Office (ICO), General Data Protection Regulation (GDPR) fines, remediation and legal costs, PR fees, customer compensations, insurance premiums, and ransomware payments. Not to mention that incidents come with inevitable downtime and opportunity costs, with internal resources pooled away from usual activity and towards remediation, all of which could be minimised or even mitigated by a swift and measured response as a result of planning.
If you’re interested in hearing more about how to respond to an incident, we’re partnering with YCSC, CAPSLOCK and Leeds University Business school to host ‘Hack to Basics: Rebuilding Post Breach’ on the 16th April 9:30 am – 12:30 am at the University of Leeds.
This event offers the opportunity to learn through interactive tabletop activities, real life case studies, and best practice, with the opportunity to meet and network with like-minded attendees whilst enjoying refreshments and lunch.
If you’re working within an organisation and want to be prepared, or are interested in learning more about incident response, this event is for you. Attendees can expect to develop a clearer understanding of how to respond to minimise loss and get back to business as usual.
This event is designed to be practical, but not technical, so no prior knowledge of incident response is required. Please sign up and join us to learn from industry experts from the field and academia!