How Can RFID Be Hacked? (And Secured!)


The radio frequency identification (RFID) market is estimated to be worth in the region of £114.4 billion. This market size includes all tags, readers and software designed for RFID cards and RFID key fobs, including all form factors. In other words, it’s big business! Yet, nearly 80% of all key cards used within commercial facilities may be prone to protocol vulnerabilities, and thus RFID can be hacked.
The physical security industry has experienced a major overhaul with advances in technology. For example, door security has evolved from simple pad locks and keys to RFID-enabled cards and fobs that can be swiped and triggered, as well as using electric locks to open doors. While this technology is amazing, it requires constant evolution and adaptation to defend against malicious users.
It’s fair to say that any new technology, from the moment it is introduced to the public, is vulnerable to manipulation and hacking by malicious actors. RFID technology was introduced to the masses in the very early noughties and by 2013 RFID technology had spread across multiple sectors. The majority of users were using what are known as EM4100 protocol cards or a CMOS IC-based cards, which has the information about the tag or fob stored openly. As these had no encryption or authentication, they would broadcast their information as soon as a reader was nearby. This posed a huge security risk as anyone with a reader and the ability to get reasonably close to a person, bag or car, for example, could copy that information and then rewrite it to a blank card or fob. Essentially, gaining access to somewhere they are not authorised to.
These key cards/fobs can be copied! There are a whole raft of products called Handheld RFID Writers (which can be purchased for as little as £15) and they work like this:

There are also HID cards, which work on 13.56 MHz and are a little more difficult to copy:
Since the frequency is significantly higher, in comparison to the 125 KHz type of cards, the volume of data bits that can be sent per second is higher. As such the data on the chip that needs to be encrypted will be greater, rendering it, in theory, more secure. As encryption is available for these cards, the way they communicate is to send a signal and the reader reads it. Unlike before, however, it no longer advertises its data. Instead, it only broadcasts data that is public — like its ID and name.
OK, so they’re slightly more difficult to duplicate, but can we still copy them? In a word, yes!
To access the sensitive information, you must provide that sector of memory with the right key otherwise it will display as blank. Even though these cards are a lot more secure, once you have a good idea as to the encryption algorithm, you can decrypt them and access the sensitive information. With that, people can also clone these cards relatively easily.

NFC reader / writer
Since the vast majority of Android smart phones have NFC (near field communication) on them, reading these cards and in certain cases cloning, them is a relatively simple process.
The easiest way to clone Mifare NFC Classic 1K Cards is by using an Android smartphone with NFC capabilities. That’s right, your mobile phone can be used to compromise the security of a company if they are using these types of cards (RFID security system). It’s as easy as downloading the “Mifare Classic Tool” for Android. With this onboard an attacker can commence cloning cards that have never had their default sector password changed. The app comes with the default keys set by the manufacturer of NFC cards, you would find it hard to believe how many people never bother to change this.
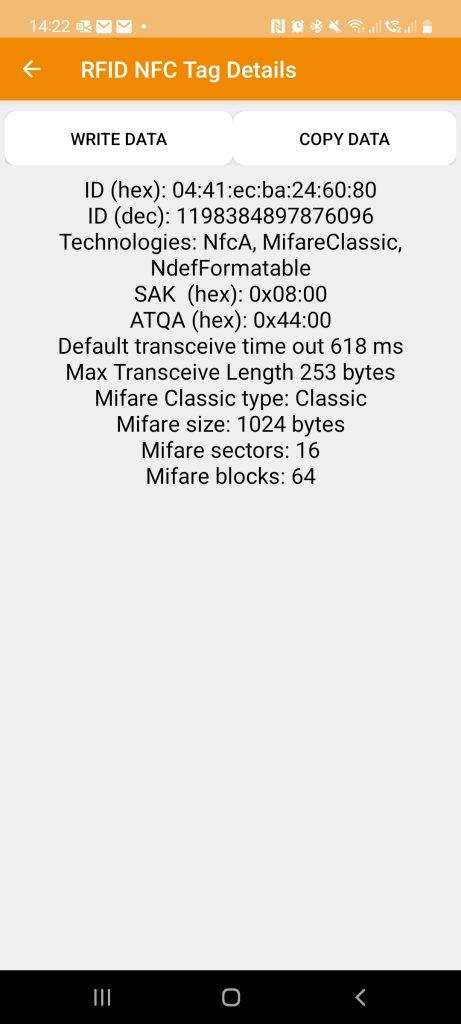
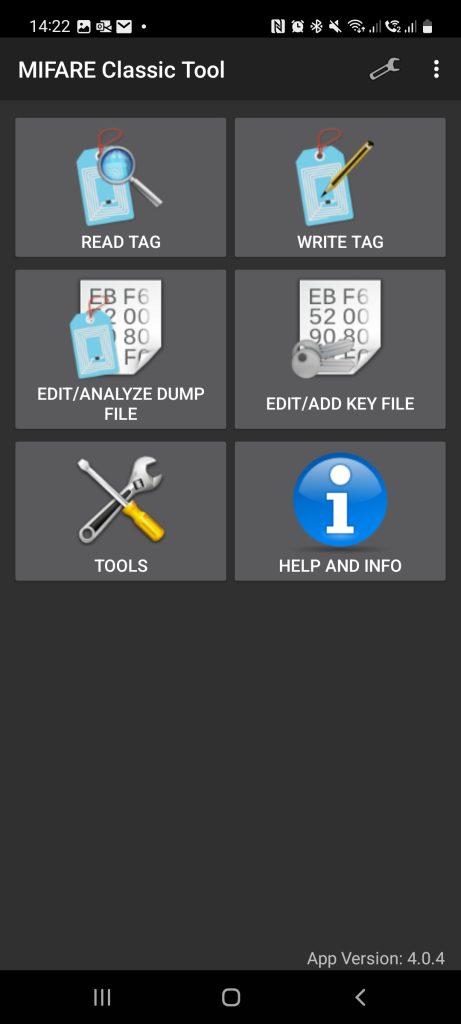
As soon as we have read the key card or fob, we can store all of the information onto a file. It is then possible to use the captured information and write it onto an empty card, essentially cloning the original card or fob. The Figure above, on the right, shows the “Write Sector” portion of the app, in which you can write individual sectors or write all of them. The important sector to keep in mind is sector 0 as it is what contains the UID and manufacturer’s data, basically if you copy sector 0 to another fob then you’ve made a copy.
So, whilst the technology has become increasing secure over the years, there’s still steps to take to protect against some of the attack vectors which can hack RFID devices. Obviously, changing all default passwords to a complex one, which has nothing to do with your company name, business or personnel within it, is essential. Just because you get a physical security company to supply your access solutions, doesn’t mean that they are following best practises. Far too many still use default or guessable passwords, basically rendering the solution nearly useless. If you’re interested in how to get people to care about setting secure passwords, you can read our blog here . Keeping key cards in a reader proof wallet or case will help prevent skimming, where an attacker gets close enough with an NFC or RFID reader.
Most importantly, physical penetration testing of security systems and practices will ensure that this attack vector is reduced to virtually nil. If this is something you’re interested in, you can request a chat with us here.