VMware vRealize Unauthenticated RCE Chain
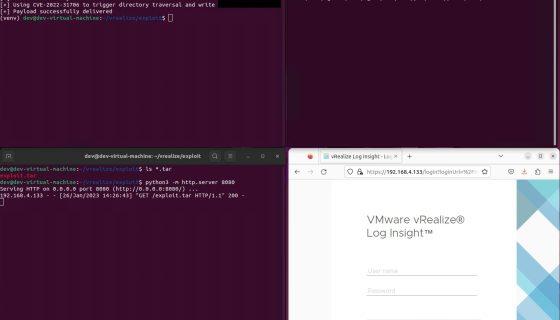

VMware recently released security advisory VMSA-2023-0001, detailing multiple vulnerabilities in its vRealize log management solution, ranging from medium to critical in severity.
However, when chained together, unauthenticated remote code execution with root privileges can be achieved. This would allow a threat actor to take full control of the victim’s machine, enabling them to perform actions-on-objectives and potentially pivot to other network devices.
These vulnerabilities were responsibly disclosed by the Zero Day Initiative; a vendor-agnostic security research collective that aims to find and disclose new zero-day flaws in software, with the goal of aiding vendors in securing their products and ultimately protecting their customers.
Soon after the official advisory was released, the Horizon3 Attack Team, part of penetration testing organisation Horizon3, tweeted an image teasing some upcoming blog posts on exploring these new vulnerabilities.
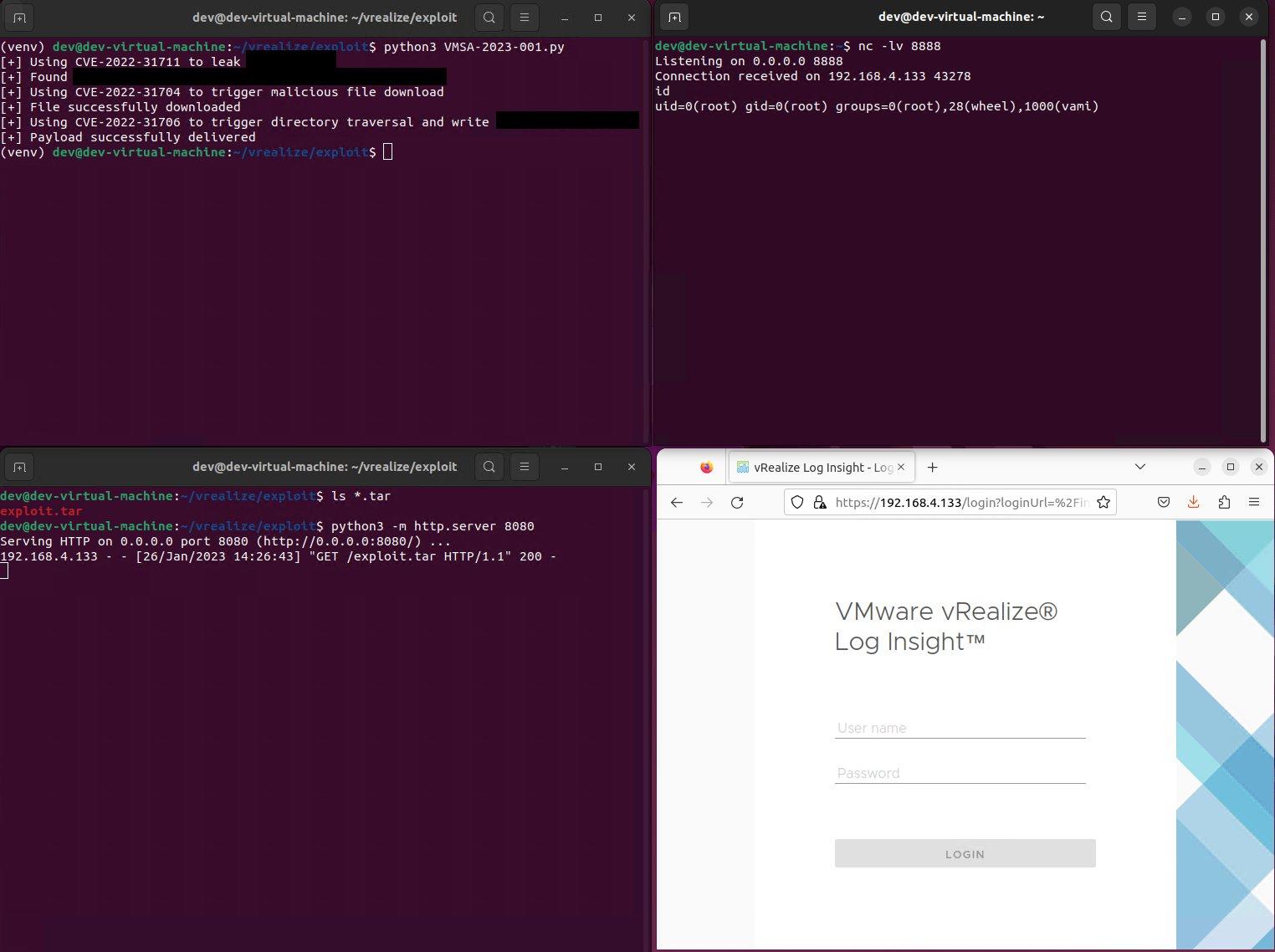
Figure 1 Exploiting CVE chain leading to unauth RCE as root
The next day, Horizon3 released a blog detailing indicators of compromise from successful reproduction of the exploit, including log entries and packets captures, as well as observing exposure of vRealize to the internet using a Shodan search, even if the vRealize system is only meant for internal network use:
Our Indicators of Compromise blog post for the recent #VMware vRealize Log Insight RCE vulnerability chain.
🔹Log File Entries
🔹Packet Capture
🔹Shodan Exposure
🔹CVE-2022-31704, CVE-2022-31706, CVE-2022-31711https://t.co/CbiXQMx1Eh— Horizon3 Attack Team (@Horizon3Attack) January 27, 2023
Shortly afterwards, Horizon3 released an additional blog post again via Twitter with proof-of-concept exploitation details. This POC is now also available publicly via Github:
Our technical deep-dive blog post for the recent #VMware vRealize Log Insight RCE vulnerability chain leading to root privileges.
💥CVE-2022-31704, CVE-2022-31706, CVE-2022-31711
💥POC exploit in posthttps://t.co/g7CxjMvHop— Horizon3 Attack Team (@Horizon3Attack) January 31, 2023
The individual vulnerabilities are outlined below with CVSSv3 scoring:
CVE-2022-31706: Directory Traversal (9.8, Critical)
CVE-2022-31704: Broken Access Control (9.8, Critical)
CVE-2022-31710: Deserialization (7.5, High, not included in the exploitation chain)
CVE-2022-31711: Information Disclosure (5.3, Medium)
The impact of chaining these vulnerabilities is evidently severe, resulting in complete system takeover, however a patch has now been released (fixed version is 8.10.2) for the affected product so this should be applied as soon as possible. Where this cannot be done immediately, a workaround is also available via the official advisory. Additionally, blue teams are able to track in-the-wild scanning of these vulnerabilities by monitoring this GreyNoise tag.
If you want to know if you’re vulnerable, need help or remediate or require other mitigation services, including our XDR NAZAR X solution, and Encircle for SMBs, then get in touch or email enquiries@communicate.technology.